For years, Apple has been heralding privacy as the central theme for its products. Safari, Apple default web browser, comes with a range of privacy features to prevent websites from capturing data related to users’ browsing habits and creating personas that can be used serve them ads on other websites and platforms including — but not limited to — Google and Facebook. With Safari 15 that was launched ahead of macOS 12 Monterey and iOS 15, Apple strengthened these privacy features including its Intelligent Tracking Prevention to hide users’ IP addresses and email addresses from websites.
Primakov/Shutterstock
However, a bug in Safari and Apple’s WebKit API puts both — Apple’s reputation for privacy as well as users’ data — at risk and affects several Apple devices including the iPhone, iPad, and Mac.
The bug was discovered by FingerprintJS, a company that sells tech products such as fingerprinting tools for web admins. As per the World Wide Web Consortium, Fingerprinting is a technique used by websites to identify users and read as well as collect their data accurately even when they have turned off cookies.
Safari bug expoits a fundamental web policy
FingerprintJS notes the bug in Safari 15 exploits the IndexedDB API to steal users’ data. IndexedDB API is supported by the majority of the latest web browsers and is typically used to store a huge amount of data at the users’ end. Every time a user browses a website, they interact with the database of the website, which is invisible to other websites.
In order to prevent crucial user data from being shared between devices, many web-based products follow a Same-origin policy (as defined by Mozilla Foundation). The policy limits the interaction between the components of different origins, which essentially means that a website will not share with another website any crucial data based on the users’ information.
The bug helps web products disregard the same-origin policy, and can allow miscreants to potentially steal data associated with users’ identity. Along with Safari 15 on macOS, the bug affects all web browsers on every iPhone and iPad model.
YouTube, Google Calendar among vulnerable websites
When the user visits and browses any website, the bug duplicates the website’s database with the same name in every other origin (defined above) — including frame, tab, and window. With this duplication of the database, every other website open on the web browser in a single session gets to see the data which was originally supposed to be restricted to the origin of the data. This allows other websites to get access to how a user interacted with other websites.
Furthermore, some websites like Google Keep, YouTube, Google Calendar, etc. utilize unique users identifiers. These identifiers contain information about the particular user including their login IDs. If the user has multiple Google or G Suite accounts, then the websites use unique databases for each ID. In a scenario like this, the bug can be exploited to share more than just data about which websites a user is browsing. Even without any malicious intent, other websites can at least see the display picture associated with a user’s Google account.
Even worse, if a bad actor wants to take the advantage of this flaw, they can fetch every data called by Google’s People API while logging into websites like YouTube, and the others mentioned above. They can even profile users by combining all of their IDs together and then try to take over the accounts using targeted attacks. The team says at least 30 of the internet’s top websites use IndexedDB framework, which makes the vulnerable to data leaking.
Apple yet to fix the Safari bug
The team has also created a demo webpage at safarileaks.com for users to check which websites leak their personal data. A screenshot of my account can be seen below:
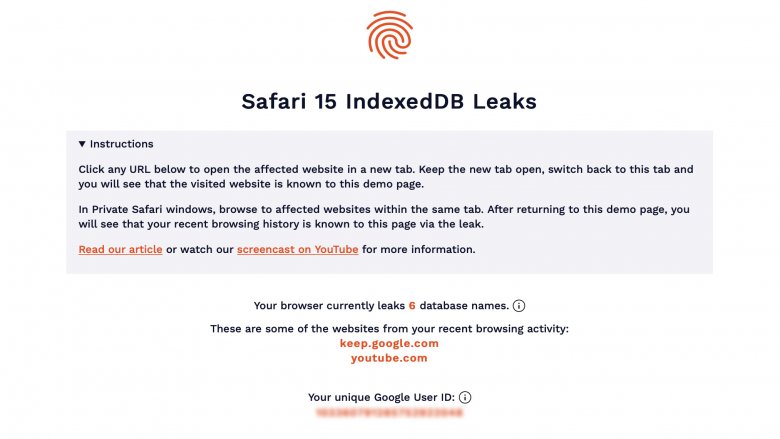
The company says it has already notified Apple via the WebKit Bugs Report center in November 2021. Apple has yet to patch this vulnerability so it may be a major concern for iOS users. Meanwhile, if you use Safari on macOS, it is advised to switch to another browser until Apple rolls out an update with a solution.







